Home | Travis Altman
Just a quick blog post to link the talk I gave at RVAsec on Purple Teaming.
Running a proper purple team
It’s now up on YouTube if you want to hear how I contextualize lessons I’ve learned in my journey.
Recently got done reading Purple Team Strategies and wanted to capture my thoughts and takeaways. The concept of Purple Teaming in cybersecurity comes from the military use of War Gaming where they pitted Red teams against Blue teams. Within cybersecuity we combine these teams, hence Purple, so that defenders can learn from attackers and vice versa.
This scenario is based upon an assumed compromise with lower privileges and after doing some endpoint recon we find a service that allows us to configure an exe of our choosing. It’s a common technique to look for vulnerable or misconfigured services as they tend to run with higher privileges. Assuming you get passed EDR with the assumed compromised some of these techniques can be noisy but are TTPs threat actors employ. I’m using Cobalt as my C2 of choice but these techniques can be leveraged with plenty of other popular C2 frameworks.
I’ll start with my overall thoughts and takeaways then get into some tips and tricks to hopefully make you more successful if you decide to tackle this challenge.
First all props go to Dominic doing all the hard work and if you want to know the nitty gritty plus different ways of getting custom stagers up and running go check out his write up.
https://dominicbreuker.com/post/learning_sliver_c2_06_stagers/
My experience is that custom stagers can help evade automated detection mechanisms but realizing it’s always a cat and mouse game these are just the steps that have worked for me as of this write up.
Was looking back through some of my notes and came across this write up I did for a Struts exploit. Nothing crazy but what I liked about the notes I captured was around detection on what defenders could have alerted on when this exploit came out. Enjoy!
Some would say what’s old is new again when it comes to a phrase like “breach and attack simulations”. How is this different from vulnerability scanning, pentesting, or red teaming? Really it’s more of a maturation of cyber security services so if your organization doesn’t currently employ a combination of vulnerability scanning, penetration testing, or red teaming then breach and attack simulations services should probably be lower on your list.
Encoding SQL injection attacks is nothing new and automated tools like SQLmap will more than likely find flaws via this method. That being said I was combing through some of my old docs and found what I think is a decent explanation how this type of attack leads to SQL injection.
TLDR: I was able to enroll a jail broken device on a “major” MDM provider. Any vendor that says they can prevent jailbroken devices from enrolling in a MDM solution is not being 100% honest. Any resourceful person can get around jailbreak detections. Because of the client side nature of this problem it’s very difficult to control the end user, as always it’s a cat and mouse game.
- Plug iPhone or iPad into Mac
- User iExplorer or iFunbox to explore file system of apps
- Export relevant directories to local box (Usually Library and *.app)
- Search for files of interest
find . -name "\*.db"
find . -name "\*.plist"
find . -name "\*.sql\*"
Search inside the files for items of interest
find . -type f -exec grep -l -i "password" {} +
iExplorer can open plist in quick view
You can open databases with Sqlite browser
One can read cookie with BinaryCookieReader.py
Just a quick tip I don’t see documented a bunch of places, when you want to feed metasploit a list of targets in a file you need to use the following syntax.
set rhosts file:/path/to/file\
This file will need to be values separated by a new line. Below is a screenshot for context.
This post will explain how to setup Burp so that you can use Python to write Burp extensions. Burp has an API that allows for extensions which add to the functionality of Burp. The Burp suite itself is written in Java so Burp natively supports Java extensions but through Jython you can now use Python scripts to build extensions. This comes in handy if you are more comfortable using Python day to day.
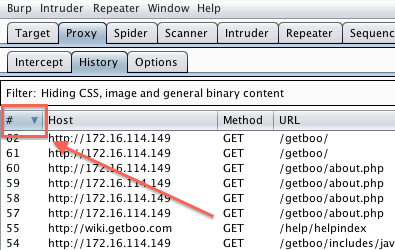
When performing an assessment of a web application I’ll spend most of my time in the History tab under the Proxy tab quite a bit. By default Burp will append the latest request to the bottom of that History log which means that I have to keep scrolling down to see my latest request to the application. This can be annoying and it’s better if my latest request were at the top of the History log. Luckily this is an easy fix with the proper sort in the History tab, simply click on the first column which will keep your latest request at the top.
When testing web applications you may come across an application that passes a ton of cookies along with each request. Cookies are used to maintain state within the application and typically only one cookie is needed within the application. There are times when other cookies are used as well and when testing web applications it may be difficult to determine what cookie is associated with session and functionality. Hopefully my technique of determining cookie functionality will also help others as well. Let’s get started with an example. I’m going to take a look at ubuntu forums as an example.
So the problem I have in my job and maybe others do as well is that when assessing a web application for vulnerabilities you want to throw automated tools at it first to get the low hanging fruit. So you get the results back and you have some good findings but you’re not exactly sure where that finding resides inside the application. Meaning first click here, then here, then here, and modify parameter X. It’s not crucial to know this because with burp or any decent web proxy we can replay that request to retrieve and prove the vulnerable results but when dealing with laymen and even developers you have to hand hold them through the exploitation process via the browser as much as possible hence the need to know where in the application the vulnerability exists.
One of the areas you need to focus on when performing security / penetration testing on iOS applications is what information is written to disk or stored locally. There are a number of things that can be written to disk (text files, config files, plist files, databases, etc). There are a handful of directories that an application typically uses to store local data within an iOS device which you’ll need to keep in mind when combing through the local file system. I’ll cover these directories and walk through an iOS application security assessment.
Some of the concepts I’ll be covering will be new to some people and may be hard to understand but for others who are familiar with this field will find the concepts simple. Hopefully no matter what your comfort level or experience you’ll get something out of this.
When performing security testing on a Windows environment, or any environment for that matter, one of the things you’ll need to check is if you can escalate your privileges from a low privilege user to a high privileged user. No matter what environment you are testing there are going to be a range or roles with varying privileges, for the most part on a local windows environment there going to be three roles / privileged users.
So this is the final article in this series of honeypots and honeyd and before I wrap it up I’ve gotta give big shout outs to Neils Provos the creator of honeyd. Neils has done an excellent job with the honeyd program and his book Virtual Honeypots is hands down the best book about honeypots and I highly recommend picking up a copy. While writing some of these tutorials Neils was even kind enough to answer some of my emails.
All the information I’m about to go over is nothing new, I’m just trying to organize all my notes on pen testing mssql. Hopefully my notes will help others. All the commands and instructions are Linux based so keep that in mind.
So up to this point you’ve probably only ran honeyd on your laptop or desktop machine. If you want to get the most out of honeyd then you’ll probably want to run it on either a server or an embedded device. In the beginning of this series I mentioned you could run a honeypot in a number of ways. Two of the ways I mentioned was to attract malware to a vulnerable system so that you can analyze the latest and greatest malware. The other way was to attract attackers on your network. In my series I’m going to keep the focus on detecting attackers on the local network and not trying to find new malware. The honeynet project already does a great job of tracking down the latest and greatest malware so check that project out.
It’s rare during a penetration test that I actually exploit a vulnerability to gain more information. Newcomers to my filed will often use the term “network security”. I don’t care about the network, have the network for all I care. What I’m more concerned about is the information inside the network. The better way to describe it is “information security”. Performing penetration tests one has to keep that in mind, yea it’s fun to exploit some user that’s running an old version of war-ftp but if that user doesn’t yield sensitive information then who cares to some extent.
In the past two tutorials I’ve used DHCP to obtain IP’s for our honeypots running honeyd. Using dhcp is fine when testing honeyd and getting familiar with how honeyd works but a static IP may be more suitable for your environment. In my case I initially fooled around with honeyd via dhcp but when I wanted to implement in a more production environment I realized that static IP’s are more stable and less maintenance. In order to ping our honeypot the router / switch has to know what IP and MAC address our honeypot has so it can update it’s information, going through dhcp does this automatically. I’ll touch on how to add the static IP configuration later but first let’s go over our layout. I’ll be using the same simple layout as in the first tutorial as seen below.
Part one of this series was to mainly get honeyd up and running. Hopefully you also took away from part one that the configuration file, honeyd.conf, is the key to making things work smoothly and properly. Now that you’ve got honeyd up and running let’s tweak honeyd.conf so that we have multiple honeypots running on one installation of honeyd. One honeypot is great but having three or four is even better. Part two is dedicated to showing you how to properly setup multiple honeypots in honeyd. In part one we only emulated a Windows device via the line below in honeyd.conf
If you’ve somehow found my obscure site then you probably already know a little bit about honeypots and their functionality, if not here is a good breakdown. There are many different types of honeypots and these different types are explained very well in the book Virtual Honeypots which I highly recommend you read if you are serious about deploying a honeypot.
I got tired of always searching online for the location of something in the windows registry, especially when it came to forensic analysis. Hopefully this compilation will help others to find things of interest inside the windows registry. My plan is to update this article as I find more interesting locations within the windows registry.
These add-ons are mainly related to web application security, you see these types of list related to firefox add-ons but these are the ones that I think are the most helpful. Firefox has a nice category called web application security penetration testing that has a lot of the plugins I’ll mention. Not all plugins in this category are worthwhile which is why I’m sharing my list.
When I say web app worm I mean a web site specific worm such as twitter. Twitter has been picked on (they should be because it’s a meaningless app) when it comes to web app worms so why stop now. There are other types of worms that could include web servers and databases but that won’t be addressed in this write up. The web app I’ll pick on for this example is Gruyere. Gruyere is an intentional vulnerable application that a handful of folks over at google wrote to point out some of the major vulnerabilities within web applications. Gruyere is very twitter like so my example would be relevant to other applications that function in similar ways.
People often overlook printers when it comes to information security. Truth is that a ton of useful information can be found in printers. Employees will often scan sensitive documents such as social security cards, loan information, birth certificates, etc.
The main purpose of this write up is to create a tutorial for running, installing, and analyzing results of Capture-Bat. I didn’t really want to name this article “Capture-Bat tutorial” because not everyone is familiar with the tool and what its used for. When it comes to analyzing malware there are a handful of tools that every analyst should have, Capture-Bat is one of those tools.
I had the need to generate a password dictionary that would cover every possible combination for a defined character set. I first learned to program in Python so I was going to start there first. Before writing the program I decided to Google and see if anyone else had tackled this problem via Python, turned out they had. Siph0n posted his Python code to create a password dictionary over at the BackTrack forums. I wanted to post it here as a mirror and to discuss the implications of creating a password dictionary with every possible combination. Below is the Python code.
Sometimes when you want to grab the bleeding edge version of software you’ll need to utilize subversion (SVN). You can go and read Wikipedia’s take on SVN but basically SVN can be used to grab the latest snapshot of software. Grabbing Metasploit through SVN is the best way to get the latest exploits, payload, scanners, and auxiliary components. If you were to grab Metasploit from it’s main page you would be missing a lot of that functionality, this is where SVN comes into play. Unfortunately I’m not able to grab the latest version of Metasploit because my organization has restrictive firewalls and proxies preventing me from using the SVN protocol. So the best way around this problem is to wrap the application, SVN in this case, inside of a tunneled proxy for transporting. The best implementation I’ve found for doing that is using SOCKS proxies.
So how do you manipulate a list of IP’s via the command line? Well there are several ways to go about this but I’ll present the way I went about it.
In my scenario I had a range of IP’s that I needed to extract/exclude out of a list of IP’s. This task needed to be done on a Windoze machine, I do most of my scripting on a Linux box, so I was trying to rely on the findstr command. Trying to use the findstr command to search, extract, or manipulate a list of IP’s will make you crazy. Now I’m sure there’s way smarter people out there that can craft a simple one line findstr command to hack and slash on an IP list but I’m not one of those people. I also tried to utilize some regular expression magic to manipulate an IP range. Google has this regular expression generator specifically for IP ranges, which seems neat at first but I couldn’t get it to work within findstr.
My tool of choice when it comes to fingerprinting SSL is OpenSSL. There are other tools out there such as thcsslcheck and ssl digger but in my experience these tools tie your hands when you want granular detail. It’s best to get it straight from the horse’s mouth » OpenSSL. This tutorial focuses on fingerprinting the ciphers and protocols supported by a SSL server, you can obtain tons of information from OpenSSL but this tutorial will not dig into all those aspects. Also this tutorial won’t go into the installation of OpenSSL on your OS just the usage thereof. The first step/command is to determine what kind of ciphers a SSL server may use.
Part 2 covered the neat functionality of session ID analysis within Webscarab. Now we’ll focus on another great function within Webscarab, fuzzing. I define fuzzing as testing the input of an application by trying various parameters that the input may not expect. These parameters don’t have to be random, in my opinion it’s best when you tailor your parameters depending on the application. When fuzzing you typically want to inject “command & control” parameters into the input to find the most serious vulnerability. For example if a web application is expecting a social security number I may inject html parameters such as “ < / > “ to manipulate the look, feel, and operation of a web application. I don’t want to delve a whole lot into fuzzing because there are books out there that talk about this one subject. This tutorial is going to focus on using Webscarab to fuzz web applications and find vulnerabilities. Hopefully by the end of this tutorial you will better understand the technical aspects of fuzzing as oppose to the concept of fuzzing, but more reading on fuzzing web applications may be required.
Part 1 of this series focused on the basics of using a HTTP proxy to assess a web application. I encourage people to play around with HTTP proxies with a web application that they use frequently, it’s interesting to see what information is being passed between the client and server. This communication can sometimes include your private information so it’s good to understand how that particular web application is handling your information.
This tutorial is designed to walk you through the basics of using a HTTP proxy. A HTTP proxy is very useful when it comes to web application vulnerability assessment. A proxy will allow you to record all of your transactions while using the web application producing a history of pages you have visited and links you have clicked. A proxy also allows you to see the HTTP request and responses, basically you’ll see what is being sent behind the scenes. This document will go into more detail about what a HTTP proxy can do as we step through some exercises on analyzing traffic from a web application.
I’ve seen blank administrator passwords at every organization I’ve worked. Without fail there will be some user that manages to get a PC onto your network without setting a password. This type of scenario opens up Pandora’s box into the number of vectors that could be created. Once a malicious user has control over a machine on your network its essentially game over. So as someone with security and risk management in mind you want to periodically scan for such activity, but your organization isn’t gonna spring for some fancy tool. Luckily this task can be put into a windows script that can check for this condition, see the script below.
The purpose of this tutorial is to give a quick, concise overview of how to secure your communications through a non-trusted or insecure channel. You could also use this tutorial to evade organizational firewalls and web filters but, I am more concerned about keeping my communications private rather than evading organizational filters. I have seen other tutorials that show how to accomplish tunneling http traffic over SSH but not in a very simple manner, so I hope this tutorial will accomplish this goal as well as help others. As always your feedback is welcome, either by commenting on this article or via my contact form.
At home you’re fully aware of the hosts/people that are on your network, or at least you should be. Friends and family are usually trustworthy people and you don’t have to worry about them carrying out malicious activity, but what if you aren’t sharing the LAN (Local Area Network) with people you can trust? This article will explain why untrusted LAN’s can be dangerous and what users/admins can do to protect themselves.